Why your company is a target: The economics and psychology behind modern cybercrime
If you own or manage a business in the United States and still think, “We’re too small for hackers to notice,” you’ve already slipped into their favorite target category. To many cybercriminals, small and midsize businesses aren’t unimportant; they’re ideal. They move money quickly, use the same digital systems as large enterprises, and often have fewer layers of defense.
To understand why you’re a target, it helps to see the world through a hacker’s eyes: what motivates them, how much money they actually make from a single successful attack, and why the effort‑to‑reward ratio makes business email compromise or a fake “CAPTCHA” scam so attractive.
Welcome to the underground economy, a world where a single stolen invoice or manipulated mouse click can buy someone across the world several years of financial stability.
Table of Content
Why Small Businesses Are Targeted
The Economics Behind Modern Cybercrime
ClickFix and Fake CAPTCHA Attacks
Business Email Compromise (BEC) & Invoice Fraud
How Attacks Move From Click to Cash-Out
Why U.S. Companies Are Attractive Targets
How a Security-First MSP Reduces Risk
Frequently Asked Questions
Key takeaways
- Cybercrime is driven by powerful economics. For many attackers in lower‑income regions, a single $50k, $100k payout equals several years of local income, making U.S. SMBs extremely attractive financial targets.
- The cybercrime ecosystem runs like a real business. There is a mature underground market with tool developers, access brokers, money launderers, and affiliates, all specializing and profit‑sharing in “crime‑as‑a‑service” models.
- Human‑focused attacks like ClickFix and BEC are central. Fake CAPTCHA “ClickFix” prompts trick users into running malicious commands, which then enable mailbox takeovers and business email compromise, a category responsible for about $2.8B in U.S. losses in 2024 alone.
- Ransomware remains costly even when fewer victims pay. While some data shows payout volumes dipping, the average cost per ransomware incident, including downtime and recovery, continues to rise, keeping it a highly profitable tactic for criminals.
- Disciplined controls and a security‑first MSP can flip the economics. Measures like MFA and conditional access, least‑privilege access, immutable backups, inbox rule monitoring, and strict out‑of‑band payment verification significantly reduce attacker ROI and limit BEC and ransomware damage, especially when coordinated with an MSP and rapid reporting to IC3/FBI.
The money math: the global value of your $50,000
Let’s start with the reality that drives most digital crime: simple economics.
In Russia and several other countries that produce many of the world’s technically skilled hackers, the average worker earns roughly $12,000-$15,000 per year. Even in wealthier regions like Moscow, salaries rarely exceed $1,200 a month. For a financially motivated actor in that context, a single $50,000 payout equals years of income.
That’s why demands you see on ransomware screens, $50,000, $100,000, even $200,000, aren’t random. They’re calibrated sweet spots: significant enough to change the criminal’s life, but still just low enough that many small businesses consider paying rather than spending months in recovery.
On cybercrime forums, these economics are discussed openly, like any other business venture. Access brokers sell stolen logins for a few hundred dollars. Ransomware affiliates advertise bulk “phishing as a service.” Money‑laundering middlemen (called “cash‑out” specialists) handle payments for a fee. What we perceive as criminal chaos often operates with corporate‑style structure and profit goals.
The hacker’s motivation: not only money
While cash is the main driver, it’s not the only one. Research into cybercriminal behavior reveals a blend of psychological rewards and social dynamics:
- Economic insecurity: When legitimate work pays poorly, illicit digital work feels rational, even entrepreneurial.
- Status and reputation: In underground forums, prestige comes from skill. A successful breach earns credibility and new lucrative partnerships.
- Curiosity and thrill: The challenge of breaking systems can be intoxicating, especially for technically gifted individuals seeking adrenaline or control.
- Ideology or revenge: Sometimes, hackers target specific nations, industries, or organizations viewed as adversaries.
To the attacker, this mix can make every campaign feel like both sport and salary. Low risk, high reward. The human cost, the lost payrolls, destroyed reputations, or shuttered small businesses on the victim’s end, rarely crosses their mind.
How “business” looks from their side
To visualize a hacker’s logic, imagine you’re running a small company of your own, but yours trades in stolen credentials and fake invoices instead of legitimate goods.
Your business model might look something like this:
- Market segmentation: Focus on industries that move cash fast, such as manufacturing, legal, professional services, and small financial firms. These sectors rely on trust and invoice payments rather than card transactions, which makes fraud simpler.
- Tool acquisition: Buy access to corporate email accounts or “phishing kits” that help steal them. The dark web offers subscription deals that rival any SaaS pricing model.
- Affiliate network: If you’re good at stealing logins but not laundering money, partner with someone who is. It’s the gig economy, just darker.
- Unit economics: Fewer attacks, but larger payoffs. Even if global ransom totals fluctuate, one successful strike can yield a meaningful profit margin.
Modern cybercrime mirrors startup culture more than traditional organized crime; it’s efficient, modular, and ruthlessly optimized for ROI.
Two favorite attack playbooks
Most modern attacks begin not with a technical exploit but with social engineering, tricking humans into helping the hacker. Among the countless tactics circulating online, two stand out for their simplicity and success: the fake “ClickFix” CAPTCHA scam and the old‑but‑reliable invoice fraud tactic known as Business Email Compromise (BEC).
The “ClickFix” trap: when curiosity defeats caution
“ClickFix” campaigns look innocent. A user encounters a web page, pop‑up, or email that seems to say, “Please verify you’re human to continue.” It’s styled like any legitimate CAPTCHA, perhaps with a Google‑looking logo or small loading spinner.
What’s really happening is manipulation. The user is guided through steps that appear to validate identity but secretly involve copying and pasting a short “verification code” into a system prompt. That code isn’t harmless, it’s a command that downloads and executes malware. Because the user initiates it, most corporate security tools see it as “trusted” behavior.
Once the malware runs, it’s game over. Password managers, browser cookies, session tokens, and stored email credentials are lifted silently. Attackers now own your employee’s digital identity.
Security professionals have observed this “fake verification” method spreading rapidly across platforms. Microsoft has publicly warned companies to harden systems by limiting who can use PowerShell or script execution tools, and by running awareness drills that teach users how these social tricks unfold.
The math for the attacker again makes sense: one distracted click can open doors to emails, payment details, and invoice databases, everything needed for a six‑figure fraud.
The invoice scam: cybercrime’s most profitable hustle
Business email compromise isn’t glamorous, it doesn’t involve encryption key battles or dramatic ransom notes, but it is devastatingly effective.
Here’s how it works:
An attacker either compromises a legitimate mailbox (often through a phishing or “ClickFix” attack) or creates a nearly identical domain, think “accounting@financlal‑group.com” with a subtle letter swap. They monitor ongoing email threads between the company and its vendors or clients, waiting for the right moment.
When a real invoice is due, they jump in and send an almost identical email, except for one key change: the banking details. The payment, often $50,000, $100,000, lands in the attacker’s controlled account. By the time anyone notices, the money has moved through multiple accounts and vanished.
According to FBI data, BEC caused over $2.8 billion in losses in 2024, outpacing all other cybercrime categories. It doesn’t require technical genius, just patience, psychology, and a bit of email spoofing skill.
Attackers love this method because it avoids messy encryption or file takeover drama. It feels quick, clean, and reliable. For a hacker in a low‑income region, one successful invoice fraud can literally change life overnight.
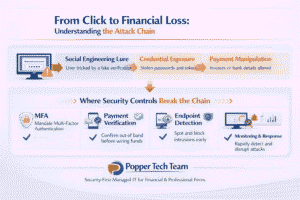
How the playbooks connect: from click to cash‑out
Most real‑world breaches aren’t isolated incidents, they’re sequences. Consider this typical chain:
- Initial access: An employee clicks a fake CAPTCHA “verification” page. Malware silently steals credentials and browser sessions.
- Email takeover: The attacker logs into the employee’s mailbox (often in Office 365 or Google Workspace) and sets hidden forwarding rules to monitor financial correspondence.
- Conversation hijack: Weeks later, when a legitimate invoice is due, the attacker slips in, changes payment instructions, and waits.
- Cash‑out: The business wires funds, $60,000 disappears, and the attacker cashes out before the bank flags anything.
- Escalation: If payment fails, the attacker threatens data exposure or deploys ransomware to extract secondary profit.
Each step relies on social engineering more than code. And because no single action looks malicious on its own, traditional firewalls and antivirus tools rarely catch the process until it’s too late.
Why U.S. companies are such magnets
From the attacker’s perspective, U.S. small businesses sit at a perfect intersection of traits:
- High transaction values: Even modest firms move large sums, routine $50k‑$100k transfers for payroll, vendor payments, or retainers.
- Speed over scrutiny: American business culture prizes efficiency, quick payments, and trust-based relationships. That means fewer verification steps.
- Vendor complexity: Multi‑layered supply chains create many touchpoints and routine invoice exchanges, ideal for impersonation.
- Perception gap: Many executives still believe cyberattacks target only Fortune 500 companies, leaving internal defenses underfunded.
This is why, from a hacker’s seat in a neighboring time zone, a Midwestern manufacturer or a regional law firm looks just as lucrative as a global enterprise, but easier to breach.
Inside the psychology of social engineering
Social Engineering, the craft of manipulating human behavior, is at the heart of every successful cyberattack. The best hackers are amateur psychologists.
Tactics like fake CAPTCHAs exploit something called “verification fatigue.” In everyday digital life, employees constantly see prompts to confirm identity: MFA codes, “I am not a robot” boxes, and update windows. The brain learns to comply automatically to get back to work. Hackers count on that muscle memory.
In BEC attacks, they rely on contextual trust. When an email thread looks authentic and arrives from a familiar address, recipients rarely question a change in wire instructions. The attacker’s voice adopts the polite, routine tone of a colleague or vendor. Psychologically, that consistency is disarming.
The lesson: you can’t fix human trust with firewalls. Only constant awareness, simulation, and training can recalibrate those reflexes.
Why partnering with a security‑first MSP changes the equation
Most businesses don’t have the internal staff or budget to keep up with fast‑evolving cyber tactics. That’s where a mature, security‑first managed service provider (MSP) becomes essential; not as a vendor, but as a strategic partner who thinks like both a hacker and a defender.
Here’s what separates a truly security‑centric MSP from a traditional IT support team:
Human‑centric safeguards
Instead of relying purely on technology, they anticipate human behavior. For example:
- Implement browser isolation to prevent fake CAPTCHAs from launching scripts.
- Restrict PowerShell and script permissions only to trusted administrators.
- Use endpoint detection tools that look for clipboard or command anomalies, tiny signs of “ClickFix”‑style attacks.
- Run tightly focused awareness programs that simulate phishing lures and “fake verification” prompts.
The goal is to make secure decisions intuitive, not exceptional.
Business email compromise prevention
Because most financial losses stem from compromised mailboxes, layered identity defense is vital:
- Mandate multi‑factor authentication (MFA) and conditional access.
- Use continuous monitoring for suspicious logins, impossible travel patterns, unfamiliar IPs, or unusual OAuth consents.
- Automate detection of hidden inbox rules and forwarding instructions.
- Require out‑of‑band (phone or verified system) confirmation for any banking change in vendor emails.
These habits shrink the BEC attack surface dramatically.
Ransomware and recovery resilience
If attackers do gain access, containment and recovery determine whether a business survives:
- Patch vulnerabilities on schedule so criminals can’t exploit old flaws.
- Apply least‑privilege identity principles, users get only the access they need.
- Maintain segmented, immutable backups stored offline.
- Test incident response playbooks quarterly.
It’s not about perfection; it’s about having disciplined response muscles when chaos hits.
Executive‑level context
Cybersecurity isn’t only IT’s concern; it’s business risk management. A good MSP translates technical signals into financial relevance for leadership teams:
- Quarterly briefings tie threat intelligence to real business impact.
- Security metrics show progress (e.g., reduced phishing click rates or MFA adoption).
- Decision‑makers learn why a $50k loss isn’t hypothetical.
When leaders see cyber risk as directly tied to cash flow, priorities shift fast.
The hacker’s return on investment, and yours
It’s sobering to realize how efficient cybercrime economics have become.
For an attacker:
- Entry cost: a few hundred dollars for access tools.
- Success odds: rising daily as AI tools make phishing more convincing.
- Payout: $50,000, $100,000 per hit, equivalent to years of average income abroad.
- Risk: low, with minimal enforcement or extradition threat.
For you, the same event can mean:
- Frozen payroll and lost vendor trust.
- Customer data exposure and regulatory fines.
- Reputation damage that outlasts the incident.

When attackers run cost‑benefit analysis, you lose, not because you’re careless, but because they’ve turned crime into a precise business model.
Reframing security as a discipline, not a defense
There’s a cultural shift all businesses must make. Security isn’t a one‑time purchase or bolt‑on service. It’s a discipline, woven into daily operations just like accounting accuracy or safety checks. That discipline has four cornerstones:
- Identity control: Protect every digital identity with MFA, strong password policies, and continuous monitoring.
- User coaching: Train employees not to fear mistakes but to report them immediately. Speed matters more than blame.
- Payment verification: Make financial controls sacred, always confirm any banking changes out‑of‑band.
- Aligned partners: Choose MSPs and vendors whose contracts and success metrics reward security outcomes, not just uptime.
These aren’t glamorous steps, but they directly counter the economics that make you a target.
Seeing the world through the attacker’s eyes
Imagine it from the other side for a moment. You’re sitting behind a cheap laptop in a rented flat outside Moscow or Bucharest. You scroll through an underground forum listing dozens of exposed corporate logins from U.S. businesses, available for $50 each. You buy ten. Three work. One leads to an Office 365 account with access to the company’s accounts payable mailbox.
You wait, watch email threads, and when a $62,000 invoice is ready to be paid, you send one altered message. The money moves before sunrise. You log off, transfer funds, and disappear.
For you, that’s three or four years of income. For the business owner in Ohio, it’s a potential bankruptcy. Both sides experience the same event through completely different economic lenses.
That’s why empathy for the attacker’s motivations helps leaders understand the risk. It’s not personal; they’re rational actors pursuing opportunity. Your job is to make that opportunity too expensive.
The quieter revolution: when small businesses fight back
Across the United States, more small and mid‑sized organizations are finally shifting from reactive defense to proactive discipline. Some invest in cyber insurance; others adopt continuous training and risk reporting. The best combine all three with the right MSP relationship.
We’ve seen regional manufacturers halt ransomware mid‑execution because their EDR flagged unusual PowerShell use. We’ve seen accounting firms recover instantly from BEC attempts because they required phone verification before wiring money.
These aren’t dramatic victories; they’re quiet wins that reshape the odds. They prove that even against a global, economically motivated threat landscape, small organizations can protect themselves with the same rigor as large ones.
The bottom line: discipline is the ultimate deterrent
For most cybercriminals overseas, your $50,000 or $100,000 isn’t just money; it’s freedom, independence, or status. For you, it’s payroll, trust, and survival. That imbalance defines modern cybercrime.
The tactics, fake CAPTCHA, invoice fraud, and credential theft are easy to dismiss until they strike close to home. But understanding what drives the attacker reframes the conversation. They aren’t mystical hackers in hoodies; they’re opportunists running profit margins.
Your defense doesn’t start with fear, it starts with structure:
- Verify before you pay.
- Educate before you click.
- Partner, before you need rescue.
Because in this ecosystem, every small business that builds discipline helps tip the economics back toward security.
Frequently Asked Questions (FAQ)
Why do hackers target small and mid, sized businesses instead of large corporations?
Hackers target small and mid, sized businesses (SMBs) because the payoff, to, effort ratio is usually better than going after large enterprises. Big organizations tend to have dedicated security teams, layered defenses, strict change controls, and mature incident response plans. In contrast, many SMBs rely on basic antivirus, simple passwords, and informal processes, especially around payments and vendor management. At the same time, SMBs still move large sums of money, tens of thousands of dollars, in a single invoice or payroll run. From a hacker’s perspective, that means they can achieve a life‑changing payout with far less resistance and lower risk of detection. SMBs also often believe they are “too small to be noticed,” which leads to underinvestment in security and creates the exact blind spots attackers look for.
How does a single $50,000, $100,000 cyberattack change the game for attackers?
The financial impact of a $50,000, $100,000 attack looks completely different depending on which side you’re on. For a U.S. business, this range can represent a critical vendor payment, a portion of payroll, or a major project milestone. Losing that amount suddenly can mean cash‑flow crises, delayed salaries, missed obligations, and reputational damage with customers or suppliers. For an attacker in a lower‑income country, however, that same payout can equal three to five years of average wages in their local economy. It can fund a significantly higher standard of living, more tools, and further criminal operations. This disparity fuels the economics of cybercrime: the attacker’s potential reward is huge relative to their cost and risk, while the victim’s loss is painful and sometimes existential. It’s precisely this imbalance that makes SMBs such compelling targets.
What is the “ClickFix” attack, and why is it so effective?
“ClickFix” is a social engineering tactic that abuses people’s trust in routine verification prompts. Instead of exploiting a technical flaw, it exploits human behavior. A user encounters what looks like a normal CAPTCHA or “prove you’re human” screen, often styled to mimic legitimate services. The page instructs them to copy and paste a short code or run a simple command as part of the verification. Because users are conditioned to click through security prompts quickly to get back to work, many comply without thinking. That code, however, is actually a script that downloads and runs malware, typically an infostealer or remote access tool. Since the user initiates the action, traditional security tools may treat it as safe, allowing the payload to slip past defenses. Once installed, the malware quietly harvests passwords, browser sessions, and email access, giving attackers a foothold for deeper attacks like business email compromise or ransomware.
What is business email compromise (BEC), and how does invoice fraud work in practice?
Business email compromise is a type of fraud where attackers gain control of or convincingly impersonate a legitimate business email account, often in finance, leadership, or accounts payable. Once inside, they monitor real conversations between the company and its customers or vendors, paying special attention to ongoing invoices and payment schedules. At the right moment, just before a legitimate payment is due, the attacker slips into the thread and sends a message that looks authentic, changing the bank account or routing details. Because the email appears to come from a trusted contact and usually matches the tone, signature, and timing of past conversations, the recipient often follows the new instructions without suspicion. The money is wired directly to an account controlled by the attacker or by a money mule, and then quickly moved or laundered through other channels. This kind of fraud can drain tens or hundreds of thousands of dollars in minutes, with little technical trace beyond an email that looked “normal” at the time.
How do ClickFix and BEC attacks connect in a real, world scenario?
In many real incidents, ClickFix and BEC are not isolated events but stages in a single attack chain. It often starts with a ClickFix, style lure: an employee sees a fake verification page and follows instructions to run a “verification code,” unintentionally installing malware. That malware steals login credentials and active session tokens, which the attacker uses to log into the victim’s email account, often unnoticed. Once inside the mailbox, the attacker sets up forwarding rules, hides certain messages, or silently observes ongoing conversations, especially those involving invoices, contracts, or payment details. Over days or weeks, they gather context, who pays whom, how much, and on what schedule. Then, at a strategic moment, the attacker intervenes in an active thread, sending updated payment instructions from the compromised account. The funds are diverted, and by the time anyone realizes something is wrong, the money has been transferred again and is difficult to recover. If the attacker wants even more leverage, they may use the same access to exfiltrate sensitive data or set up a future ransomware attack.
Why are U.S. businesses particularly attractive targets for these kinds of attacks?
U.S. businesses sit at the intersection of several factors that make them appealing targets. Financially, even small American companies often handle large transaction amounts, making each successful attack highly profitable. Operationally, many U.S. organizations prioritize speed and convenience, fast payments, trust, based relationships with vendors, and a bias toward efficiency over friction. This can mean fewer checks when bank details change or when invoices look slightly different. Structurally, U.S. businesses also tend to have complex vendor ecosystems with many third parties, contractors, and service providers, which increases the volume of email, based transactions and opportunities for attackers to insert themselves. Finally, there is a persistent perception problem: many leaders still assume cybercriminals prefer big corporate targets. That belief leads to underinvestment in security controls and user training, leaving gaps in identity protection, email monitoring, and payment verification that attackers exploit with relatively little effort.
What practical steps can businesses take to reduce the risk from these attacks?
Businesses can significantly lower their risk by focusing on a few high-impact, practical measures. First, strengthen identity security by enforcing multi-factor authentication on all critical accounts, including email and remote access, and using conditional access policies to flag or block unusual logins. Second, harden endpoints and admin tools: restrict the use of PowerShell and other scripting tools to administrators, and deploy endpoint detection that looks for suspicious clipboard use, command execution, or new scripts, patterns often associated with ClickFix, style attacks. Third, implement strict payment and banking change procedures: any request to change account details for vendor payments should be verified through a separate channel, such as a phone call to a known contact, not just an email reply. Fourth, educate staff with targeted training, not generic lectures, simulate fake verification prompts, invoice scams, and mailbox rule alerts so employees recognize and report them quickly. Finally, maintain tested backups that are segmented and tamper-resistant, and have a clear incident response plan so the team knows exactly what to do when something goes wrong.
How does working with a security-first managed service provider (MSP) help?
A security, first MSP brings structure, expertise, and continuous attention that most SMBs can’t maintain internally. Instead of just “keeping the lights on,” a good MSP designs your environment to resist the specific tactics attackers use, such as ClickFix, BEC, and ransomware. They help implement and enforce multi-factor authentication, conditional access, endpoint protection, logging, and inbox rule monitoring. Beyond technology, they create and maintain incident response runbooks so everyone knows who does what when an incident is detected. They also run tabletop exercises and live simulations, like fake verification drills and mock invoice fraud scenarios, to test your people and processes under realistic conditions. In the event of a real attack, a security-focused MSP can coordinate rapid containment steps, assist with communication, and help liaise with banks or law enforcement to improve the chances of freezing or recovering funds. Over time, they provide regular risk briefings to leadership, translating technical threats into business language, which helps decision‑makers justify and prioritize ongoing security investments.